new
Integrations Web API
Webhook Sender Validation using HMAC
To ensure that the information received in your webhook is authentic from ROOK, we have implemented a new security measure by sending an HMAC code as a
header
called x-rook-hash
as part of the information sent.This new header will only be available for version 2 of our webhooks.
What does the new header contain?
To use this functionality, our team will give you a secret hash key to create the HMAC. This key is unique to you and therefore you must store it correctly.
The HMAC code sent in the
x-rook-hash
header is the result of the union of the following information.- Client UUID (client_uuid)
- User ID (user_id)
- Datetime (datetime)
It is the union
without separators between the values
, as you can see in the example below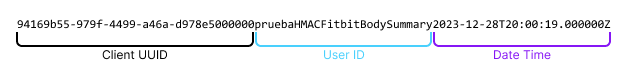
To this we add that the
secret hash key
that we have previously given you is used together with the message to generate the HMAC signature, and finally the algorithm used is HMAC with SHA-256
.That will be the value you will receive in the
x-rook-hash
header in your webhooks.It is important to keep in mind that your secret hash key is partially formed by your secret key, which means that if you change your secret key, your secret hash key will also change.
How can I validate it?
You can validate quickly using the following online tool.
To know if the value sent by ROOK is real, you will need to repeat the above process on your system internally. An example is shown in Python to be able to validate the hash by taking a summary of the body.

To validate that the process is correct you can try this?
- Hash this text: ROOK
- Use this as a secret hash key: ROOK_Secret_Key
- Use SHA-256as Digest Algorithm
- This should be the result: 382da6381717a0fdfeba9ef922041df3ea8db97bbd2d20af21e216bdd1e6096b